Intercepting Desktop Application Via Fiddler
GT;DR
Thick client application security testing is a crucial process for ensuring the security and integrity of software applications that run on end-user machines. These “fat” or “rich” client applications often have a GUI that communicates with a remote server or database, making them vulnerable to a range of security threats. Desktop applications are software programs that are installed on local computers or workstations. They are different from web applications, which run over a network or the internet. Examples of desktop applications include word processors, image editors, and financial software, among others. While desktop applications have many benefits, such as faster performance and greater control over system resources, they are also susceptible to security risks.
Challenges intercepting Windows Store app traffic 👻
When you download a desktop application from Windows Store, it may be difficult to intercept its traffic in tools like Burp Suite or Echo Mirage, depending on how the application is designed and how it communicates with servers.
It may be difficult to intercept traffic from a desktop application is that it may use a different protocol or communication method than traditional web applications. For example, it may communicate over a custom protocol, use a proprietary encryption method, or use binary data formats that are not easily readable by tools like Burp Suite or Echo Mirage.
Additionally, some desktop applications may be designed to prevent interception of their traffic for security or anti-piracy reasons. They may use techniques like SSL pinning, which prevents the interception of SSL traffic, or code obfuscation, which makes it difficult to reverse-engineer the application.
Overcoming Desktop App Traffic Intercept Obstacles🪓
In our case, We analyzed the traffic of a desktop application downloaded from the Windows Store using Wireshark. During our analysis, we observed TCP traffic, but we encountered issues when attempting to intercept it using Echo Mirage, as the application crashed. We also attempted to intercept the traffic by configuring the system proxy with Burp Suite, but were unsuccessful. The invisible proxy method was also unsuccessful in our attempts to intercept the traffic.
We then started searching other methods for intercepting traffic from the application. We went through many blogs and forums, but did not find the right solution. Finally, we came across a solution on the internet that suggested using Fiddler to capture network traffic between the internet and test computers.
Fiddler
Fiddler is a powerful proxy server that can capture traffic from any application that supports HTTP or HTTPS traffic. By setting Fiddler as the system proxy, we were able to intercept traffic from the desktop application without any issues. We could see the requests and responses in clear text, and we could also manipulate the traffic using Fiddler’s built-in tools.
Pre-Requisites:
Let’s Get Started:
1.) First install the applicaton from the Windows Store.
2.) Install the Fiddler from the site.
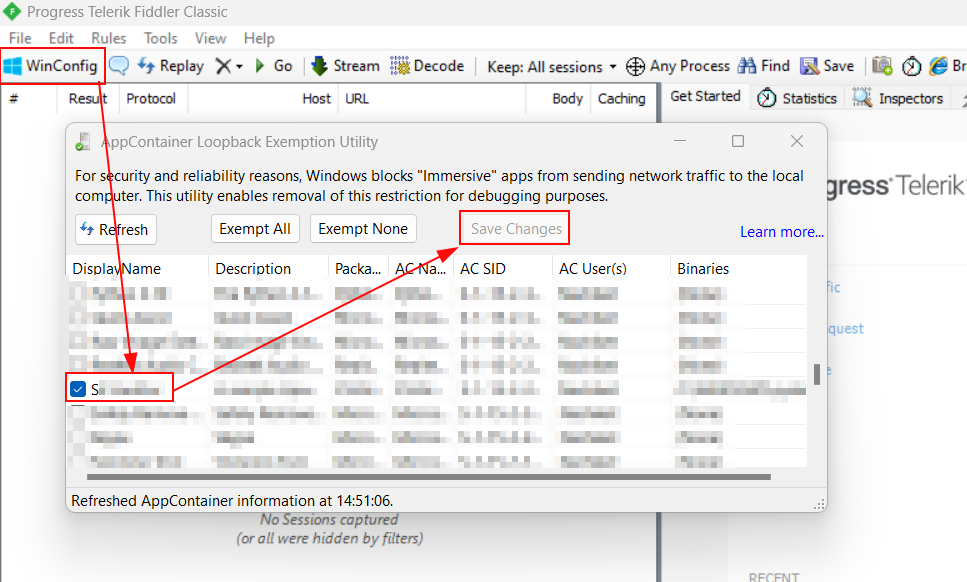
3.) Now configure the Fiddler to intercept the traffic from the Windows applicaiton.
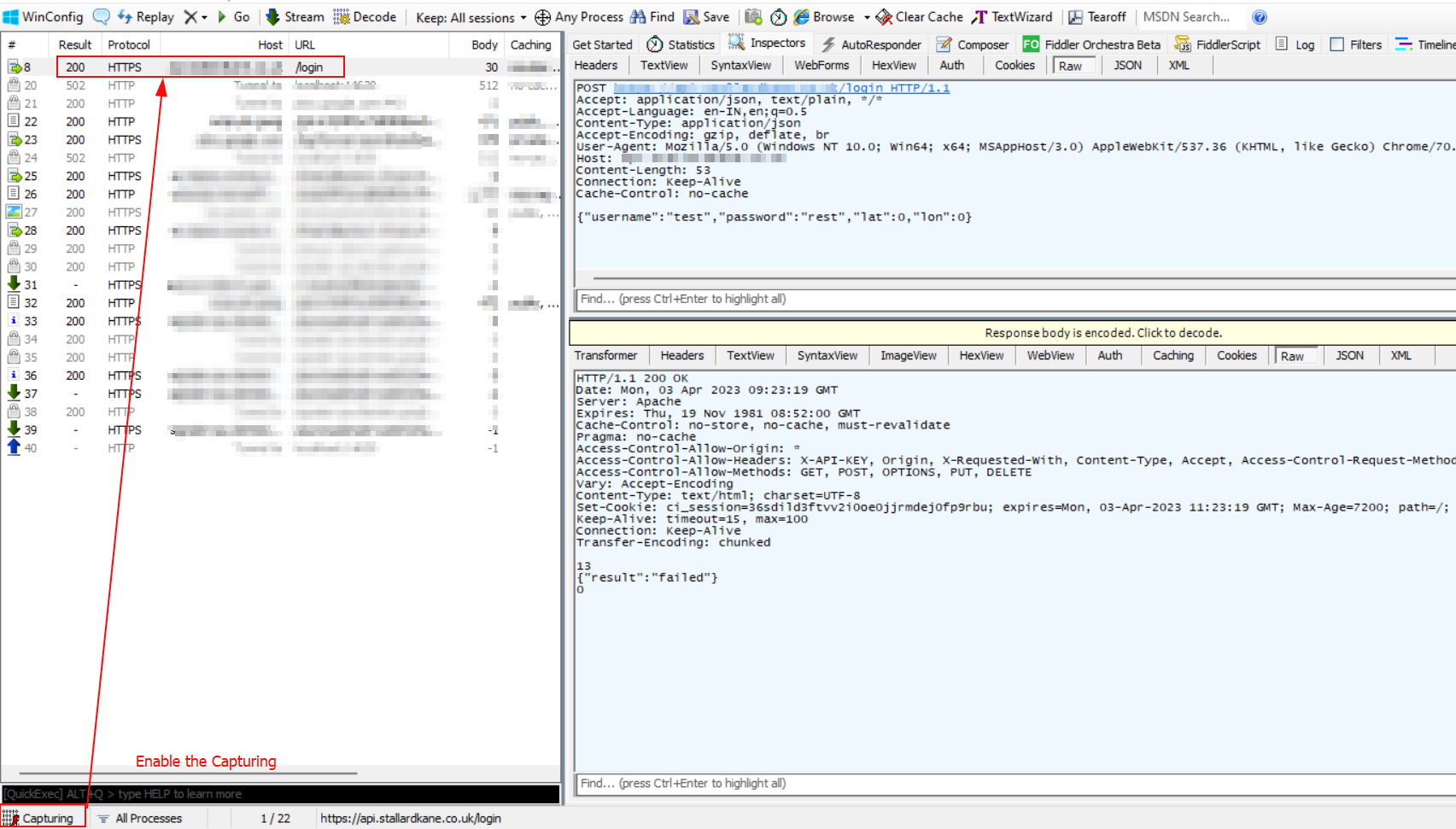
4.) Now enable capturing and launch your applicaiton.
5.) Now, Go to the Tools –> Gateway –> Manual Proxy Configuration, and setup the proxy. Also setup the same way in Burp Suite(All interfaces).
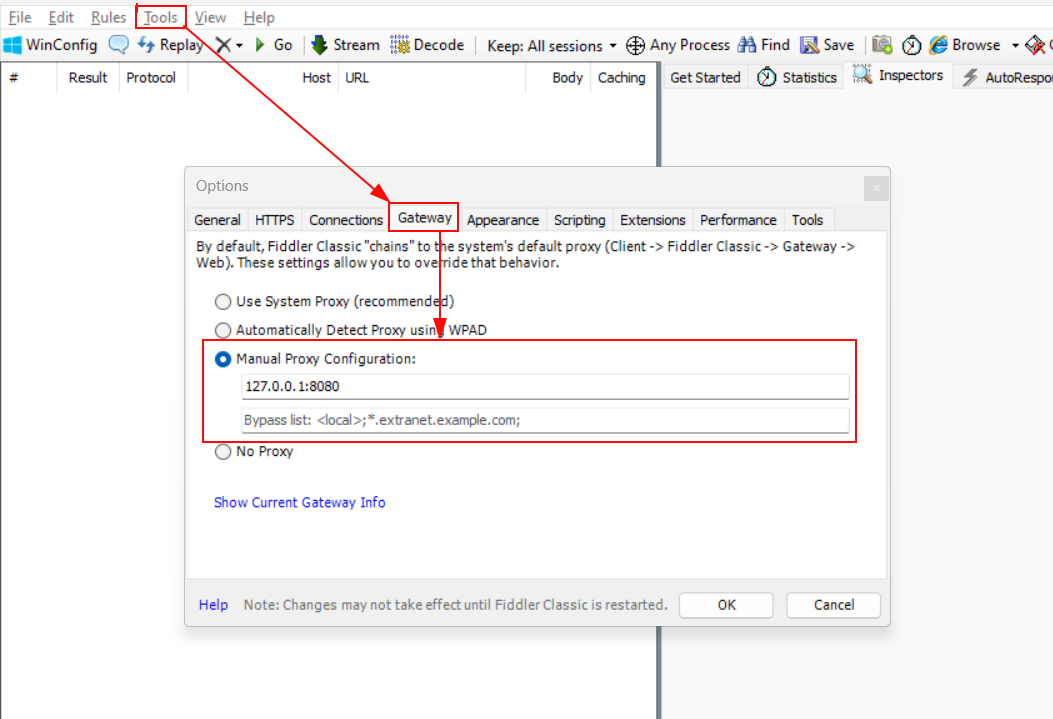
6.) Now, agin launch the application, try to intercept the traffic in Fiddler and observe that we can now be able to see the traffic in Burp as well.
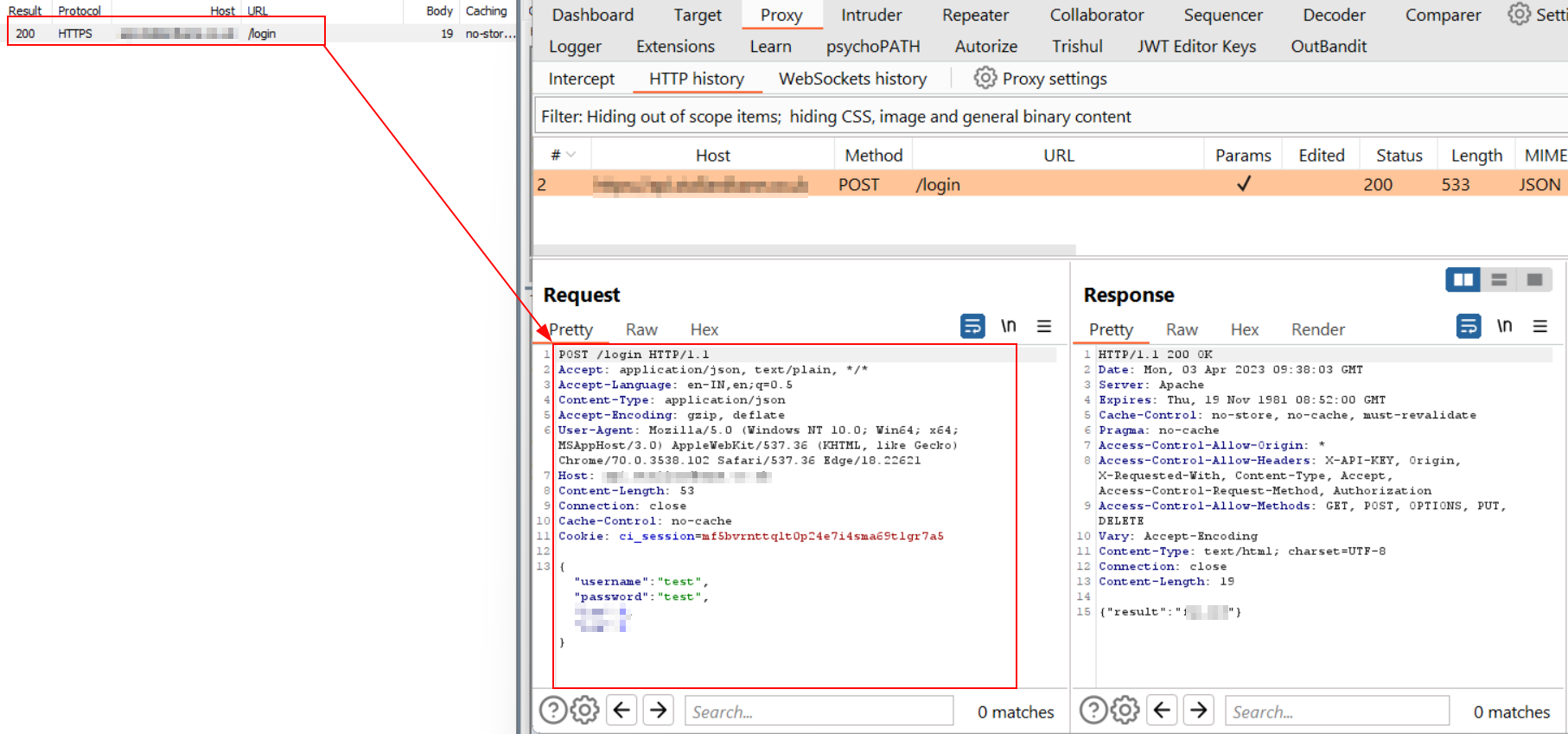
Note:
When fiddler ask for install the certificates accept the necessary ones and it will automatically set-up the rest. some of your enterprise applications might notice the proxy change and stop working, but at least you can get through your test.